Black Kite -Third Party Risk Management (TPRM) Platform Overview
Provide full visibility into yours, your suppliers and partners cyber position
The Black Kite platform was built to provide full visibility into yours, your suppliers and partners cyber position, using the same open-source intelligence tools and techniques hackers use. It uniquely combines three types of assessments to provide more fidelity and streamline the process of assessing your risks
Slide title
Write your caption hereButtonSlide title
Write your caption hereButton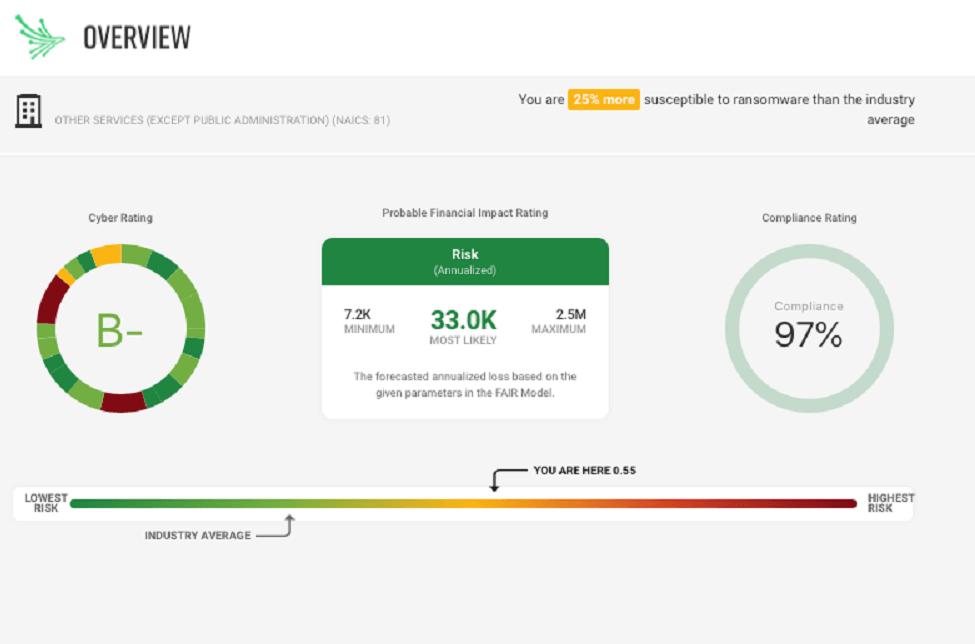
Slide title
Write your caption hereButtonSlide title
Write your caption hereButtonSlide title
Write your caption hereButton
Slide title
Write your caption hereButton
How does the Platform work, and what does it Identify?
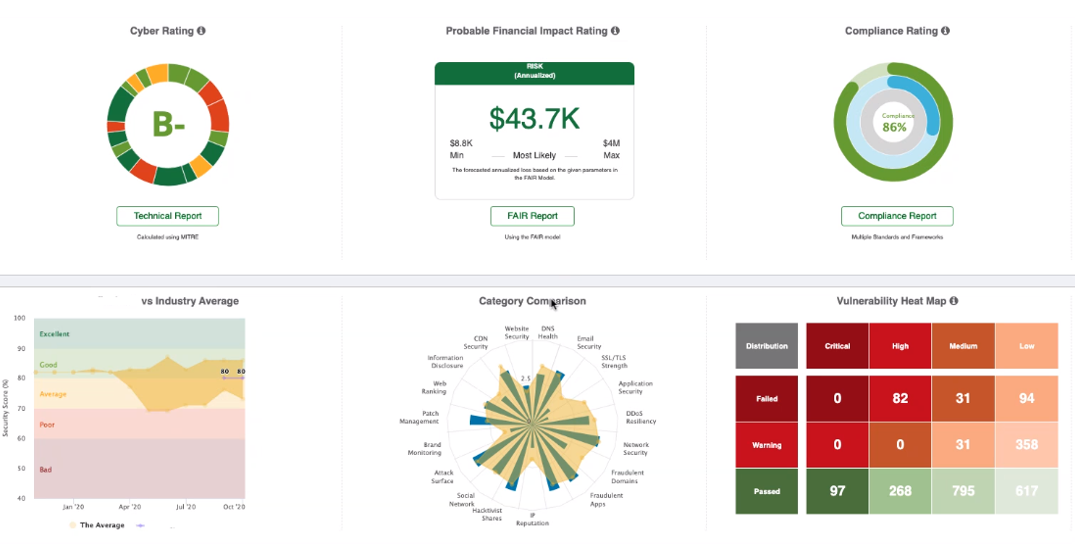
The black Kite platform examines the target domain and infrastructure landscape to identify and assign a score across three main areas, Financial Risk, Technical Risk and Compliance Risk. This process does not touch the target environment, no agents or appliances installed whatsoever.
The Cyber Risk Assessment Platform uses open-source intelligence (OSINT) techniques to collect data from 400+ OSINT resources from a span of internet-wide scanners. As an authorized IP zone transferer with one of the largest IP & Domain Whois databases, we hold more than one billion (1B) historical items. The asset-discovery engine discovers all company-related IP address ranges and domain names. The Platform uses standard scoring models like MITRE Cyber Threat Susceptibility Assessment (CTSA), Common Weakness Risk Analysis Framework (CWRAF), Common Weakness Scoring System (CWSS), Common Vulnerability Scoring System (CVSS), and Factor Analysis of Information Risk (FAIR). Mining data from other sources enables our customers to eliminate false positives and audit results.
Three areas of Assessment
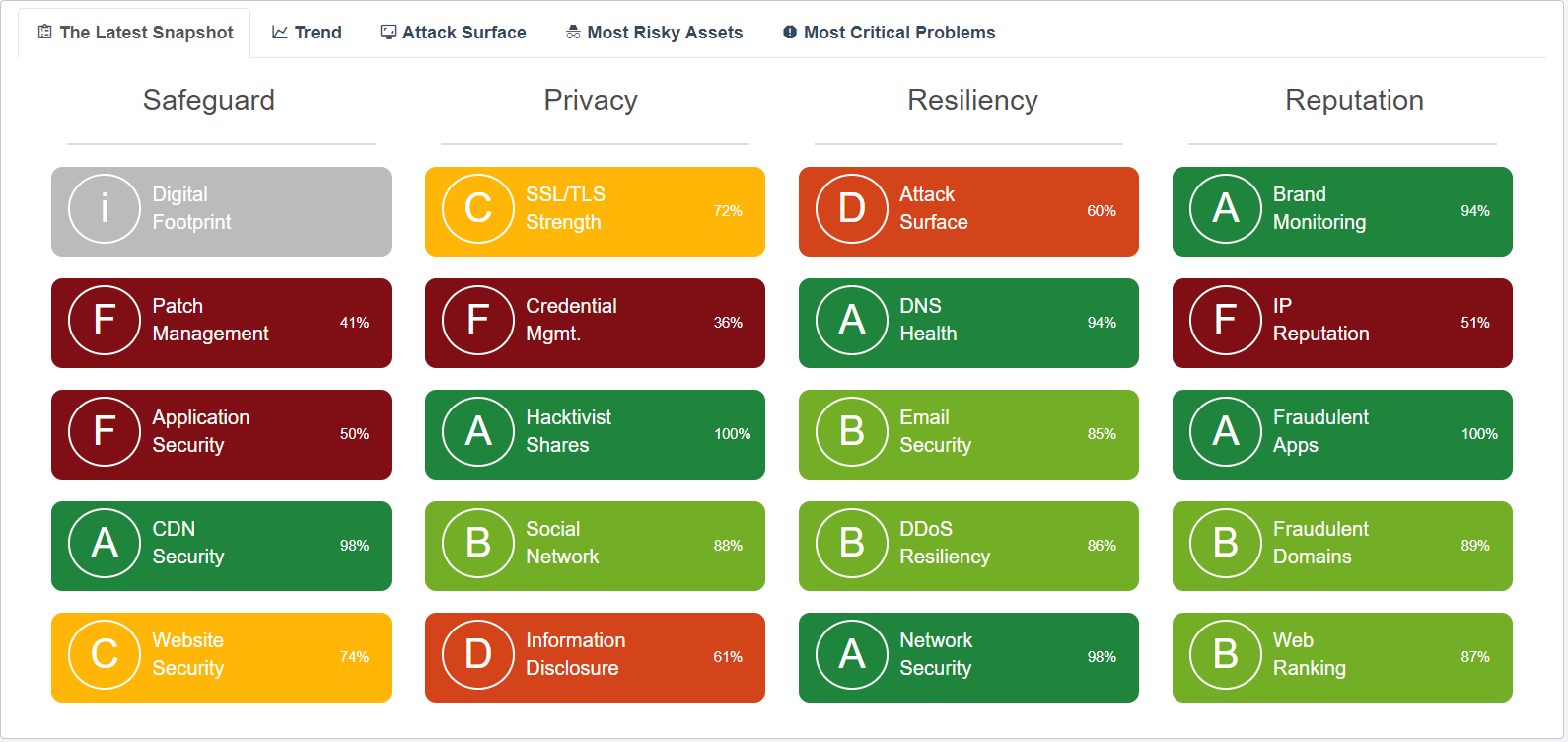
Technical Risks
Easy-to-understand letter grades and defensible data details behind 20 technical risk categories (see below). The non-intrusive report passively evaluates third-party vendors and cyber insurance subscribers and does not touch an organization’s systems or network assets. The platform follows and applies commonly used frameworks developed by the MITRE Corporation for scoring software weaknesses in a consistent, flexible, and transparent manner, converting highly technical terms into business language for executives.
Financial Risk
For the first time, CISOs, CROs, CFOs and Finance Directors have an automated tool that measures the probable financial impact of cyberattacks against your company, your suppliers and trading partners. Reports can then be easily generated to communicate the risks in financial terms and easy-to-understand business terms. The Financial Risk model is based on Open FAIR™ which is the only international standard Value at Risk (VaR) model for cyber and operational risk.
Compliance Risk
Based on Industry standards - NIST 800-53, ISO27001, PCI-DSS, HIPAA, GDPR, and Shared Assessments the platform compliance classification allows you to measure the compliance level of any company for different regulations and standards. The platform then estimates the external compliance of each company and then the cross-correlation capability measures the compliance level of your company, your supplier and business partners based on standard input, saving time and effort for both you and your supply chain. You can also upload evidential proof (questionnaires, Information security policies, GDPR guidelines, process documents etc etc) parses and processes them and automatically map the content to known standards (GDPR, NIST, ISO27001, PCI/DSS etc) giving you a clear picture of their compliance and risk to you without having to analyse each suppliers documents, saving time, money and effort for all.
Technical Risk Categories

Compliance Categories
The classification allows you to measure the compliance level of any company for different regulations and standards, if a third party is compliant with a regulation or framework, the vendor can then upload evidence documents (SIG and map data) to the platform and then estimates the compliance level for the other regulations and frameworks using prior compliance standards including the following:
ISO27001, GDPR, PCI/DSS, HIPPA, NIST 800-53, NIST CSF, NIST 800-171, CCPA, CIS CSC-20, COBIT 5, CMMC, NY DFS, OTA 217 and shared assessments
Results are Understandable and Simple.
Simple Reporting
You can perform a bulk importation of your entire supply chain and generate reports for Technical, Financial and Compliance Risk in a matter of minutes. They are then automatically graded with a letter-grade score to help identify and then mitigate potential security risks. The data can then be analysed and compiled into simple, readable reports for supply chain reports, detailed company reports, or remediation reports. You can also schedule each type of report and have them automatically sent to the right stakeholders within your business or directly to the supplier if required.
Supply Chain reports
A standard report that will give you every vendor, supplier, and 3rd party in one single pane of glass dashboard. You can then sort and rank each supplier based on what is important to you. You can also do a supplier bulk importation and have results and generate reports for Technical, Financial and Compliance Risk in a matter of minutes. Once imported and assessed, you can then flag risky suppliers (according to your own defined internal thresholds) for action and then share the reports with your suppliers and create tickets to delegate any necessary follow ups or interventions.
Detailed Company reports
Get a detailed single report on each supplier showing the risk to you and then drill down into each of the individual sections for compliance, technical or financial risks. You can then share the platform with your suppliers so they too can see their detailed results.
Remediation reports
A standard report that will give you a step-by-step process to reduce the risks associated with each company, this also shows the probable decrease in financial risk and increase in security posture. You can then flag these risky suppliers to CCS to do a free Rapid Assessment and Monitoring Process (RAMP) to work with the supplier to improve their security and reduce the risks to you. This will enable the business to decide on investment of time and effort to improve the overall security posture, while simultaneously reducing the risk.
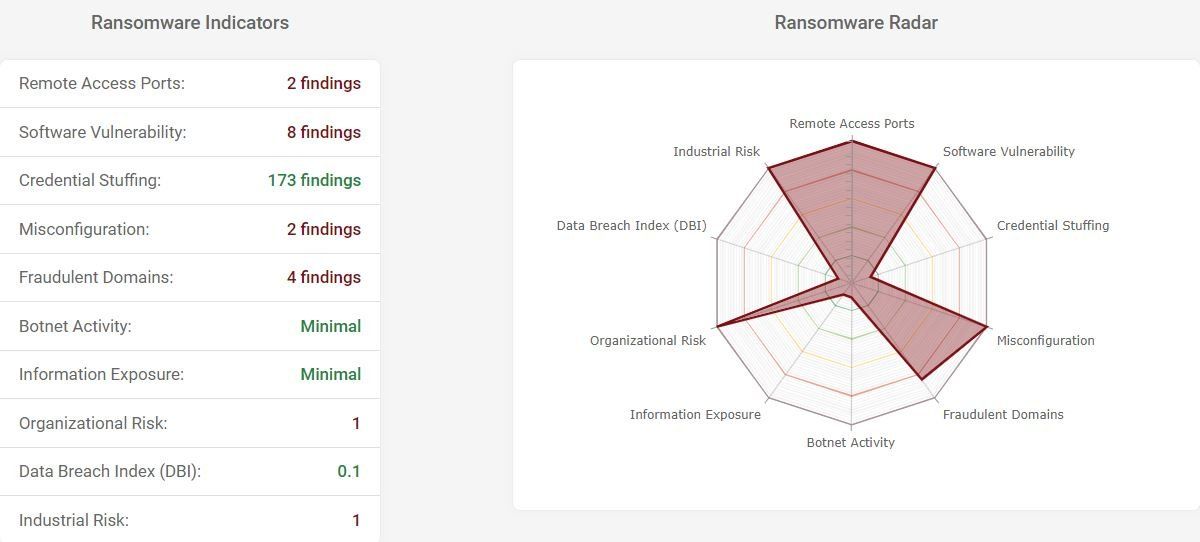
Ransomware Susceptibility Index (RSI):
The Ransomware Susceptibility Index (RSI) is a new metric in the platform that provides the probable Ransomware risk associated with a monitored company. The RSI is the result of curating numerous statistical Ransomware sources and technical ransomware indicators to present to you an "Early Warning System" for possible ransomware activity.
Need a proof of value
For you to validate the platform we can provide a full Proof of Value for up to 5 of your suppliers . This will enable you to get a full understanding of the platform and to see your suppliers susceptibility they are to a ransomware attack as well as their security, compliance and financial risk to you in the event of a breach.
The Proof-of-Value step are straight forward and are defined as follows:
- Complete and return the Risk Assessment Questionnaire
- Agree a success criteria
- CCS run an on-line Rapid Assessment of the chosen 5 suppliers
- Joint live demonstration against the provided suppliers
- CCS present Supply chain overview reports
- CCS Present individual company reports against each supplier
- CCS Present remediation reports for each supplier
- CCS Present feedback and measures against success criteria
Free Risk Assessment
Do you know the risks that you face, or the risk your suppliers pose to you? Try a free risk assessment to understand the level of detail we can provide for Technical, Compliance and Financial risks.
Key findings from the reports we will share with you about you, your chosen supplier or partner, are as follows:
- Their overall Cyber Rating Score.
- Their compliance rating across 14 frameworks
- What would be the financial impact to you if they are breached
- How susceptible they are to a Ransomware attack
- Potential improvements in Cyber Security and compliance
- Potential reduction in financial risk to you, if there was a breach.
- Their benchmark in their industry?
- Their Cyber Security vulnerabilities.
- Their Cyber Security heat maps.
- Many more valuable technical, compliance and financial risks.
Company Registration Number: 12789332
All Rights Reserved | Cyber Consultancy Services (CCS)